Every week we bring you various compliance checks like PCI-DSS, HIPAA, ISO 27001 and SOX so as to make our readers aware of the various checklists that businesses need to follow in order to be compliant with it. Today we will discuss about FISMA.
What is FISMA Compliance?
FISMA stands for the Federal Information Security Management Act (FISMA). It was signed into law part of the Electronic Government Act of 2002. This act is required for the federal agencies to develop, document, and implement an information security management program for giving safeguard to their information systems which even includes those who are provided or managed by another agency, contractor, or third party.
Why was FISMA Created?
FISMA was created in order to enable all the federal agencies to be able to create and fully implement a thorough information security plan and safeguard their operations. FISMA comes under larger legislation known as the E-Government Act which aims at uplifting the awareness regarding the necessity of cybersecurity and its impact on the assets of the country.
Under the Federal Information Security Modernization Act, FISMA was amended by the congress in 2014. This amendment modified FISMA based on current security concerns. It also asked the federal agencies to implement stronger measures in terms of security and pay more attention to regulatory compliances.
Who Needs to Follow FISMA Compliance?
When it was initially announced, FISMA applied only to the federal agencies. But with time, the law has gradually incorporated state agencies like insurance, Medicare, and Medicaid also. Moreover, companies who work with federal agencies are also obliged to follow FISMA. So, the private sectors companies must adhere to these guidelines in order to get contracts from federal agencies.
Must Read- Glance At The United States Cyber Security Laws
Purpose of FISMA
The National Institute of Standards and Technology (NIST) and the Office of Management and Budget (OMB) are assigned specific responsibilities by FISMA in order to strengthen information security systems. The head of each agency is required to implement policies and procedures to cost-effectively reduce information technology security risks to an acceptable level.
National Institute of Standards and Technology (NIST)
NIST is responsible for developing standards, guidelines, and associated methods and techniques for providing adequate information security for all agency operations and assets, excluding national security systems. NIST works closely with federal agencies to improve their understanding and implementation of FISMA to protect their information and information systems and publishes standards and guidelines which provide the foundation for strong information security programs at agencies.
Good Read: What is NIST Cybersecurity Framework? ( CSF )
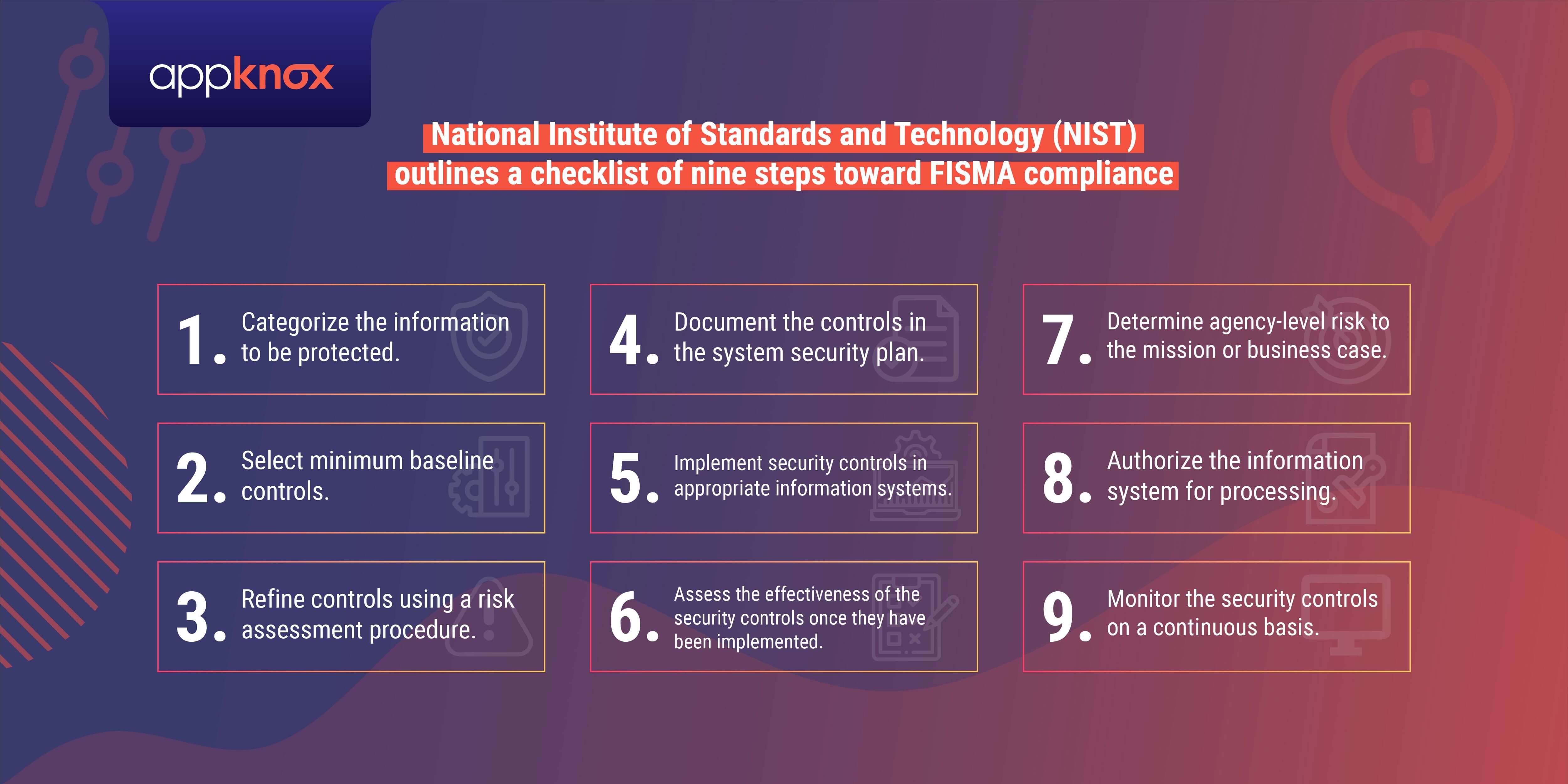
NIST outlines nine steps toward compliance with FISMA:
-
Categorize the information to be protected.
-
Select minimum baseline controls.
-
Refine controls using a risk assessment procedure.
-
Document the controls in the system security plan.
-
Implement security controls in appropriate information systems.
-
Assess the effectiveness of the security controls once they have been implemented.
-
Determine agency-level risk to the mission or business case.
-
Authorize the information system for processing.
-
Monitor the security controls on a continuous basis.
Information Security Program
This program’s main objective is to ensure that the core information security principles namely confidentiality, integrity, authenticity, non-repudiation and availability of information and information systems are provided. The key elements of the program can be summarized as below:
1. Assignment of Responsibilities
This ensures that the right officials are assigned security responsibilities.
2. Periodic Assessments of Risk
This includes the risk and consequent impact on the agency and would eventually result from the unauthorized access, disclosure, use, disruption, destruction or modification of information and information systems supporting an agency’s operations and assets.
3. Policies and Procedures
The policies and procedures are being made to reduce the risks and to ensure that the security of information is addressed throughout the life cycle of each organizational information system in a properly documented manner and this type of procedures include detecting, responding, reporting to security incidents and procedures to ensure continuity of operations.
4. Security Awareness Training
All the personnel including the contractors are required to be trained in regards to information security principles and the security risks related to their job requirements, and an agency’s policies and procedures.
5. Periodic Testing and Evaluation
The test should be done annually after some days that the effectiveness of information security policies, procedures, practices.
A Process for Planning, Implementing, Evaluating, and Documenting Remedial Actions: It also has a process for addressing any deficiencies that might occur in the information security policies, procedures, and practices of the organization which needs to be implemented and documented by the agency.
What are the benefits of being FISMA Compliant?
Enterprises have developed a fatalistic attitude towards compliance. They believe that chasing compliance might divert their time and resources from achieving optimum business efficiency.
Being compliant with the FISMA guidelines ensures that the agency's data security issues are covered. Moreover, it also ensures the safety of user data and substantially reduces IT-related costs as well. But, adapting FISMA compliance is a must to unleash several business benefits mentioned below:
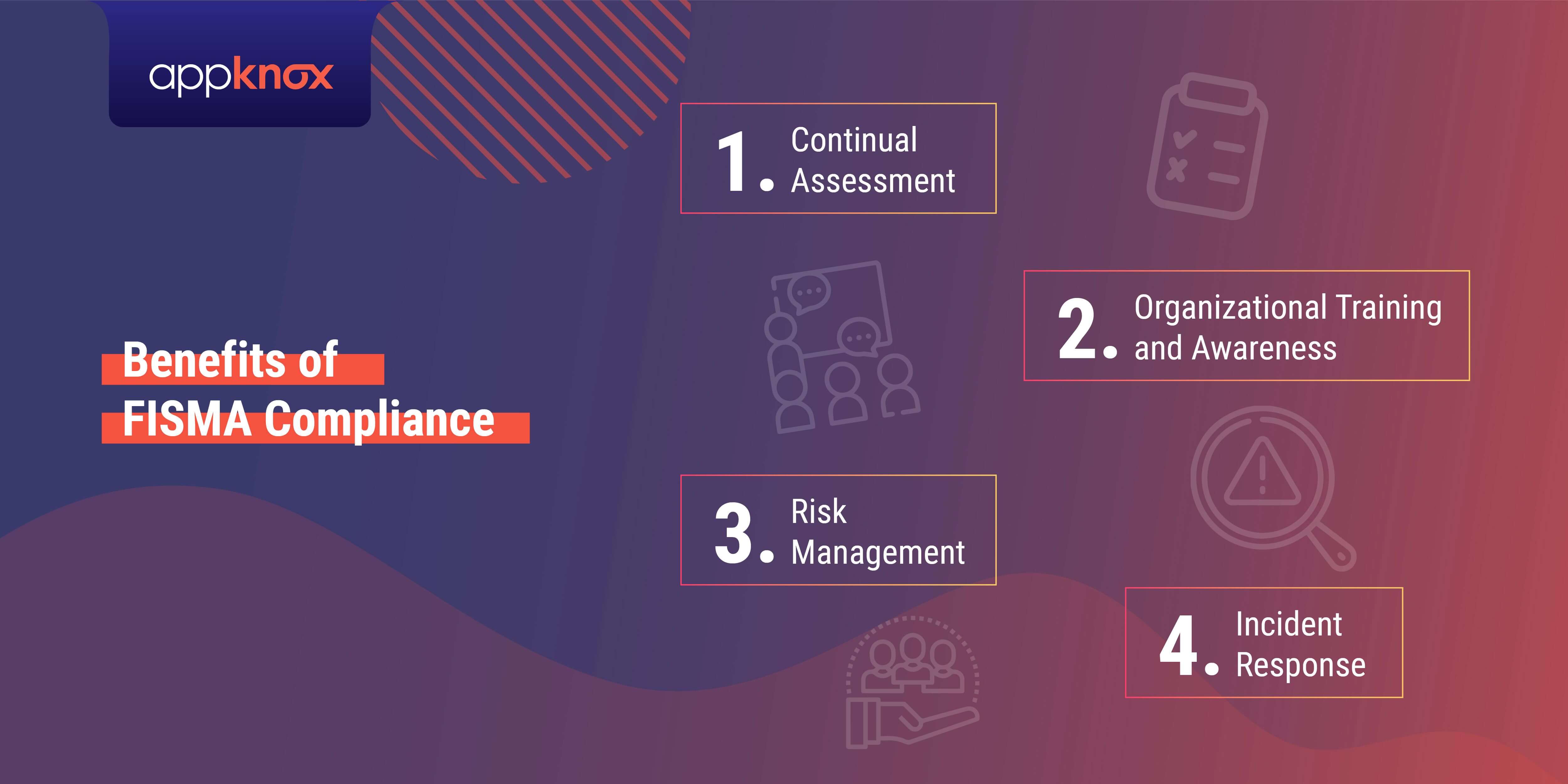
1. Continual Assessment
FISMA compliance assures that the federal agencies and related organizations develop and implement a data security program incorporating regular scanning, monitoring, and updating all cybersecurity policies. Implementing a threat monitoring program for all systems and assets assures establishing a robust patch management system and highlights all cyber vulnerabilities real-time. Along with this, it helps in resource allocation to combat evolving threats.
2. Organizational Training and Awareness
Unaware human assets with a lack of proper training are the softest target for cyber attackers. FISMA addresses the issue of inadequate problems by requiring all federal agencies and related organizations to implement and develop an ongoing data security training program. Adding a dedicated information security training program enables businesses to create a sufficiently strong organizational culture and cybersecurity posture.
3. Risk-Management
The core of FISMA is the implementation and development of a risk-management centred approach to data security. Using the FISMA model, businesses unveil the looming threats, making vital operational decisions regarding their risk appetite.
With FISMA compliance, organizations can create a stout framework for a long-lasting data security program that is flexible to adapt to current and future threats.
4. Incident Response
FISMA explicitly necessitates organizations to create and implement a well-planned incident response program. Threat detection and mitigation techniques strengthen the security posture of organizations, creating a comprehensive cybersecurity program. Designing and implementing an incident response plan makes organizations more resilient towards probable cyber threats.
Failure to Comply
If anyone fails a FISMA inspection, then it might have the following negative consequences:
-
Significant administrative sanctions
-
Computer breaches
-
Unfavorable publicity
-
Reduction of IT budget
There are many who can help federal agencies with all the requirements mandated by FISMA compliance.
Information Security Program Gap Analysis
The gap analysis of them is to help review the agency information security program and then identify it for the deficiencies and gaps that prevent the agency from achieving compliance.
Information Security Program Implementation
Enterprise Risk Management (ERM can provide support and guidance for the implementation of the information security program including the following key components:
-
Perform Risk Assessment
-
Develop and/or review Policies and Procedures
-
Provide Security Awareness Training
-
For testing and evaluating the security controls
-
For creating and documenting a formal agency-wide remediation program
How do I become FISMA compliant?
To be FISMA compliant, enterprises need to update stringent data security controls organization-wide, guided by the NIST framework:
- Risk Categorization: The FIPS 199 documents help categorize all the organization’s risk and security requirements. Each agency is directly responsible for assuring the highest level of security standards detailed in this document.
- Information System Inventory: FISMA pushes every agency to maintain their inventory across all systems, using their associated integrations.
- Risk Assessments: The Risk Management Framework (RMF) defined by FISMA, needs to be referred to whenever an agency makes any system change. This makes it mandatory to perform a three-tiered risk assessment based on the RMF guidelines.
- System Security Plan: FISMA makes it compulsory for all businesses to have a well-defined security plan that is regularly updated as per requirement.
- Security Controls: NIST 800-53 has 20 security control measures pre-defined that each agency must implement. Adopting these measures are compulsory to assure FISMA compliance.
- Accreditation and Certification: FISMA makes it compulsory for each agency to conduct annual security reviews. Agencies need to demonstrate that they can maintain, monitor and implement systems to be ultimately FISMA compliant.
- FedRAMP Program - A new government program named the Federal Risk and Authorization Management Program (FedRAMP) standardizes the cloud-computing services for agencies to be FISMA compliant. All software vendors wishing to work with the US government agencies need to abide by the FedRAMP authorization programs.





 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Harshit Agarwal
Harshit Agarwal










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

