On 12th May 2017, while the world was busy making plans for the weekend, a massive ransomware cyber attack managed to cripple more than 200,000 computers across 150 countries. Known as WannaCrypt - the global ransomware cyber attack locked up and affected essential services including the FedEx in the US, Telefonica in Spain and hospitals in Britain.
The ransomware was identified to be a new variant of 'WannaCrypt' which exploited a known bug in the operating system of Microsoft Windows and had the potential to spread automatically across various large networks by making use of the above exploitation.
Many security experts are warning against a second wave of attack that might magnify in this new week ahead with employees returning back to offices and switching on their affected computers.
"This is one of the largest global ransomware attacks the cyber community has ever seen," said Rich Barger, director of threat research with Splunk, one of the firms that linked WannaCry to the NSA.
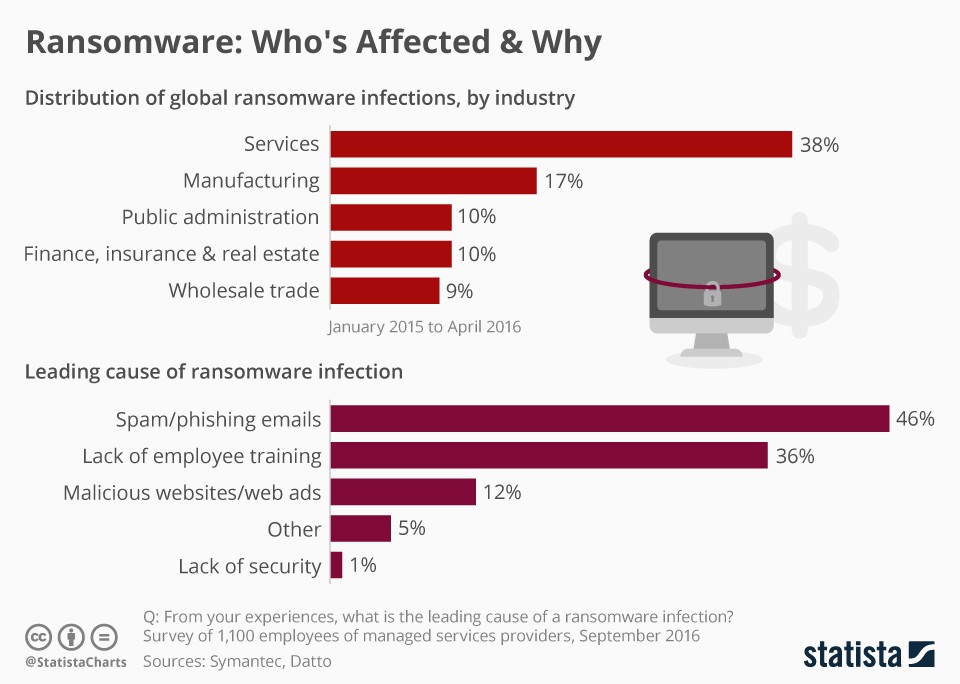
In recent years, almost every industrial sector has been affected in some way or the other by ransomware. There are however some specific types of companies that are far more vulnerable or more often targeted by these cyber criminals trying to extort money for data than others.
The analysis by Symantec below shows that the services sector in 2016 was the sector that was by far most affected by ransomware.
WannaCrypt - the Global Ransomware Cyber Attack
Also known as WannaCry, WanaCrypt0r, WCrypt, or WCRY, this ransomware exploits a vulnerability in the older versions of Windows that was originally exploited and discovered by the U.S. National Security Agency(NSA) as an offensive cyber-weapon.
"This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," wrote Microsoft President Brad Smith in a blog post on Sunday where he stressed on the need for urgent collective action to keep people safe online.
"We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage."
How did this Ransomware Spread So Much Faster Than Others?
Unlike WannaCrypt, the typical ransomware threats do not spread that rapidly. WannaCrypt is the first of its kind ransomware which acts also like a worm. This means that it gets into your computer and looks for other computers to try and spread itself as far and wide as possible.
Email or social engineering are the primary attack vectors for threats like WannaCrypt. They leverage on these and rely on users downloading and executing a malicious payload. However, in this unique case, the ransomware perpetrators used exploit code that was available publicly for the patched SMB “EternalBlue” vulnerability, CVE-2017-0145, which can be triggered by sending a specially crafted packet to a targeted SMBv1 server. This vulnerability was fixed in security bulletin MS17-010, which was released on March 14, 2017.
The spreading mechanism of WannaCrypt is borrowed from well-known public SMB exploits, wherein the regular ransomware was further armed with worm-like functionalities. This created an entry vector for all machines that were still unpatched even after the fix had become available.
WannaCrypt exploits code was designed to work only against Windows 7 and Windows Server 2008 (or earlier OS) systems that were unpatched, so this attack didn't affect the PCs with Windows 10.
Good Read: Ransomware as a Service (RaaS) & Its Implications in 2021
WannaCrypt Ransomware
The WannaCrypt threat makes use of the following 2 components that arrives in the form of a dropper Trojan:
1) A component that attempts to exploit the SMB CVE-2017-0145 vulnerability in other computers
2) The ransomware known as WannaCrypt
The ransomware component is a dropper that contains a password-protected .zip archive in its resource section. The document encryption routine and the files in the .zip archive contain support tools, a decryption tool, and the ransom message. In the samples analyzed by Microsoft, the password for the .zip archive was found to be “WNcry@2ol7”.
When run, WannaCrypt creates the following registry keys:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\<random string> = “<malware working directory>\tasksche.exe”
HKLM\SOFTWARE\WanaCrypt0r\\wd = “<malware working directory>”
It changes the wallpaper to a ransom message by modifying the following registry key:
HKCU\Control Panel\Desktop\Wallpaper: “<malware working directory>\@WanaDecryptor@.bmp”
The malware's working directory then creates a number of files anda randomly named service as shown in this blog post by Microsoft.
After completing the encryption process, the malware deletes the volume shadow copies by running the following command:
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
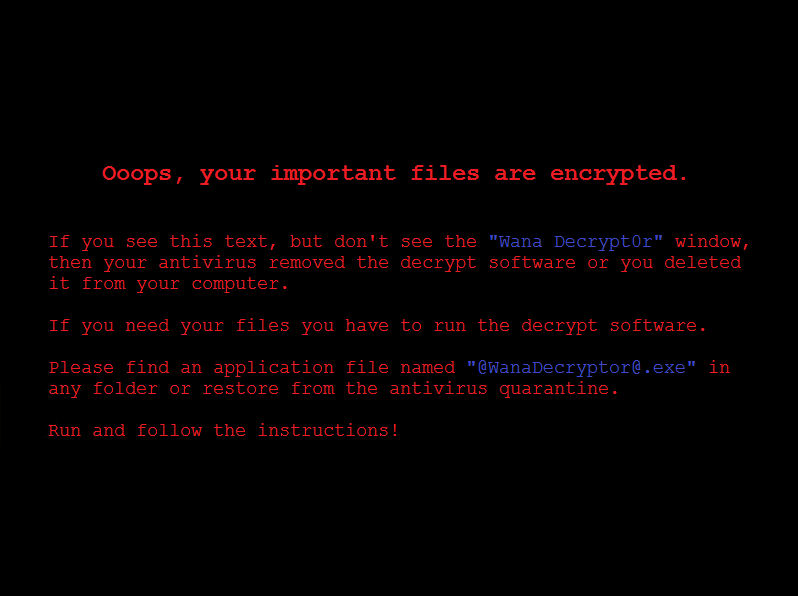
It then replaces the desktop background image with the following message:
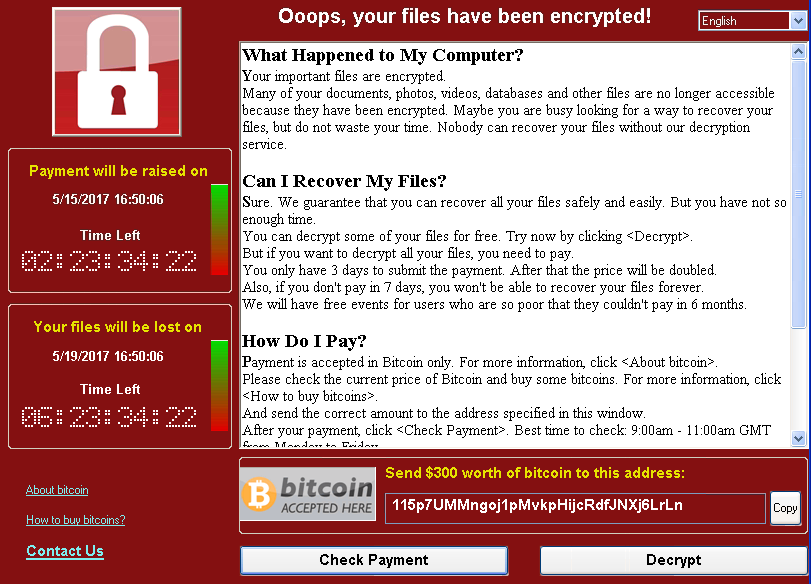
It also runs an executable showing a ransom note which indicates a $300 ransom in Bitcoins as well as a timer:
The text is localized into the following languages: Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, and Vietnamese.
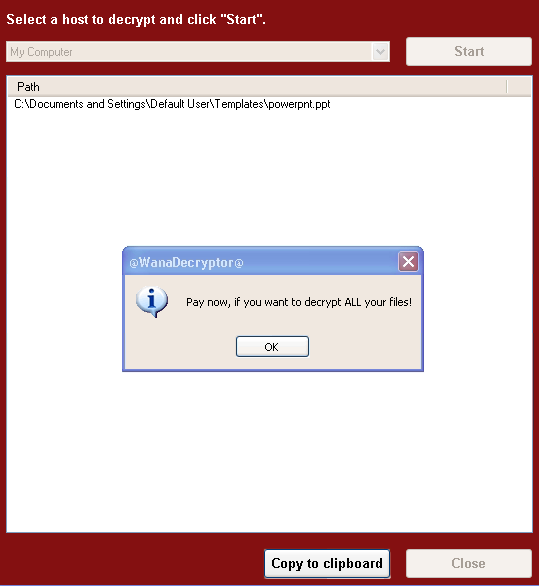
The ransomware also demonstrates the decryption capability by allowing the user to decrypt a few random files, free of charge. It then quickly reminds the user to pay the ransom to decrypt all the remaining files.
Wannacrypt live status can be seen on the MalwareTech botnet tracker. This tracker shows maps that display the geographical distribution of malware infection and time-series graphs of online and new bots. The live map displays a blip every time an infected computer pings one of the tracking servers by MalwareTech.
How can Businesses & Users Protect themselves against the WannaCrypt attack
Computers that are running on Windows 10 are safe from this threat. WannaCrypt targets only those running on older versions. It is advisable for businesses and users to upgrade Windows to the newer versions and keep them up-to-date by enabling automatic updates to be downloaded as soon as the company launches it.
Users that have not yet installed the security updates yet are recommended to install MS17-010 as soon as possible. The attack surface can further be reduced by two possible workarounds:
- Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547 and as recommended previously
- Consider adding a rule on your router or firewall to block incoming SMB traffic on port 445
Pro Tip - Older Windows OS that are no longer supported by Microsoft are dangerous to run in an online context. Windows XP, for example, has been unsupported for years and has many vulnerabilities that can be exploited by cyber criminals. For the WannaCrypt case, Microsoft has made the necessary software available that can protect machines running on these unsupported systems. If you're running Windows XP, Windows 8 or an older version of Windows Server, you can get the updates here.
A Wake-Up Call?
Microsoft President Brad Smith highlighted that the WannaCrypt cyber attack should be taken as a wake-up call for the tech sector, the consumers, and the governments to be more proactive and work together in order to protect against these cybersecurity attacks. More collective and collaborative action needs to be taken and this needs to happen right now. Everyone should participate and accept their individual responsibilities in answering and adhering to this wake-up call.
Source - Microsoft, CNBC, Stuff.co.nz, Statista





 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Erika Rykun
Erika Rykun










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

