Pokemon Go is nothing less than a sensation around the world right now. Apart from the game itself, Pokemon Go security risks are also taking the world by a storm. According to a real-time tracker built by AppInstitute, the game is fetching around 15,000 downloads every minute and bringing in roughly $100,000 every four minutes. On the other hand, Pokemon Go security risks are the other talk of the town with businesses and even governments getting worried about the risks involved.
In just a few weeks since its launch in app stores, Pokemon Go has been downloaded by more than 30 million smartphone users worldwide. While it’s a game and it’s meant to be fun, some security experts are warning that the risks may not be worth the reward for capturing Pikachu.
Indonesian officials have warned that 'Pokemon Go' is a "national security threat," and military headquarters have banned personnel from playing the game while on duty, according to Jakarta Post.
Meanwhile, in Egypt, there is a heated debate that Pokemon Go security risks are a significant threat to national security. Ahmed Badawi, deputy head of the communication committee, urged Egyptian officials to consider banning the game because it allegedly exposes the country's important security sites to the world.
Even in the U.S., the operations security (OPSEC) division of the U.S. government urges process intelligence officers and other government workers follow to protect unclassified information that could be used by adversaries to cause harm. In general terms, this means that everyone should be aware of what they are posting on social media, emails, in fact, anywhere in public.
Since Pokémon Go uses account information and location, it is a good enough reason why military officers and government workers should be mindful of OPSEC requirements. Six days ago, in fact, an anonymous member of the military posted to Reddit’s r/pokemongo forum to ask other servicemembers if the game presented an OPSEC concern.
Why are Pokemon Go Security Risks a Concern for CIOs and CTOs
Why should CISOs and security professionals care whether employees spend their spare time hunting Pokémon? Because every app an employee installs on a mobile device that they also use to connect to the corporate network and handle sensitive data can put an enterprise at risk.
Access to Sensitive Information
To be honest, it's not just Pokemon Go. Many such apps are sitting on millions of devices, and they are all a threat. Most users do not check what permissions they provide to many such apps. And whenever these devices enter the enterprise network they create havoc for the CIO. Increasingly, enterprises are adopting BYOD (Bring Your Own Device) practices which open up the network to possible external threats through devices used by employees. This provides the ability for unauthorized “actors” to access the company's networks.
According to security research firm the Ponemon Institute, roughly 69% of employees use personal devices for work purposes, which also amplifies security risks for businesses that allow employees to use corporate accounts or servers on their mobile devices.
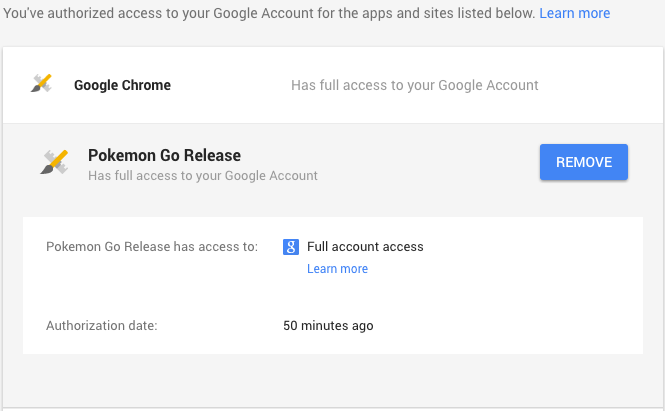
Looking at the security permissions tied to a Pokemon Go player's account shows that the game has "full account access" automatically. For iOS users, there's no option to edit these permissions; the only option is to revoke access entirely.
For people playing on Android, the game doesn't show up under Google account security permissions at all. The Google Play store includes a list of information Pokemon Go may have access to, however, including "accounts on the device" and "full network access."
What does "full account access" mean?
It is exactly what it sounds like. When you grant full account access, the application can see and modify almost all the information in your Google account. Needless to say that such access should be provided to only those applications that we trust completely and especially those that are installed on your personal computer or device.
Adam Reeve, one of the first to report this, said that Pokémon GO was granted full access to his Google account without explicitly asking for permission. Reeve said, “And they have no need to do this - when a developer sets up the ‘Sign in with Google’ functionality they specify what level of access they want - best practices (and simple logic) dictate you ask for the minimum you actually need, which is usually just simple contact information.”
Note: On July 12, Niantic Labs pushed an update to the Pokémon GO app in the Apple App Store. That update, version 1.0.1, “fixed Google account scope.” Now it is accessing basic information and not full account access. Basic information includes your profile information on Google and email address.
Malicious Versions of Pokemon Go
Other Pokemon Go security risks brought to the surface is counterfeit versions of the app in markets where the app is not yet available (outside the U.S., Australia, and New Zealand). Attackers are taking advantage of this fact and continually publishing new, malicious versions of the app. Users in countries where Pokémon GO hasn’t yet officially launched may “sideload” the app from unofficial sources and put themselves at risk.
CISOs and security professionals need to establish processes and technology that give them visibility into the devices that connect to the corporate network, the apps installed on those devices, and the vulnerabilities and other risks associated with those apps. Sometimes apps that seem harmless can easily cross the line and put an enterprise at risk.
Precautions You Should Take
Here are a few practical steps which users can take to prevent the underlying security threats in games like Pokemon Go and other malicious apps in general.
1. Grant only the necessary permissions:When it comes to permissions, it’s better to check what are the essential permissions the app needs and only grant those. Giving full access to your device information may put your own identity at risk and allow threat actors to steal your personal data.
2. Don’t download versions of apps from unknown sources:In the case of Pokemon Go, it was not released worldwide at the same time. So, in other places, people used unauthorized sources to download the game. This act of downloading apps from unknown sources opens up a new window of vulnerabilities as hackers generally inject malware into such apps.
3. Try not to root or jailbreak your device:Rooting or jailbreaking sounds so cool to smartphone users. Generally, people root their device in order to gain ‘superuser’ capabilities. But, this also gives apps the permissions to make changes to files in your system. So, before hackers capitalize on this opportunity and break into your device, it’s better that users avoid rooting their device in the first place.
4. Regularly update your device and backup your data:In order to avoid security vulnerabilities, it’s best to update your device whenever prompted. This keeps the security loopholes in checks and limits all the possible threats. Moreover, backing up personal data gives you a chance to deal with the worst-case scenario - when your device succumbs to malicious apps.
5. Invest in antivirus software:In most of the cases, users have no idea what malicious apps are doing to their device and their personal data in general. Using efficient antivirus software saves users from such scenarios and protects their device from getting into the grip of malware and other threats.
How to Ensure Security in VR and AR Apps?
AR and VR offer an amazingly immersive experience. But at the same time, they pose high-security risks like social engineering attacks and corporate espionage. The most interesting fact is that they convince the human brain in whatever way they want and create opportunities so that human vulnerabilities could be cashed upon.
AR and VR systems continuously store and transmit personal data of users. And this is, by far, the most valuable commodity for hackers. Threat actors can also target them for DDoS attacks and this can cause serious problems in critical situations where AR is used like medical procedures and sensitive machinery operation.
Another issue with AR and VR apps is that they do not encrypt their data by default. And moreover, they connect with other third-party apps whose own security protocols are questionable. So, when it comes to dealing with their security, it is better to use the same administrative and technological measures.
It is advised to include them in standard risk assessments, keep their systems and firmware updated and encrypt all the sensitive data that they hold or transmit. But despite these security measures, they pose some other unique challenges as well, especially in terms of physical safety and security.
In the case of VR devices, the auditory and visual connection of the user with the outside world is completely cut off. So, it's really important to evaluate the safety of the user in such a scenario. This also applies to AR and it becomes essential to establish a fair amount of situational awareness. Simply stating - never let your users run around blindly in busy or crowded places while looking for Pokemons.
Learn how Appknox can help protect your business from security threats masked by Pokemon Go.




 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Harshit Agarwal
Harshit Agarwal










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

