A new cybersecurity threat called Petya ransomware is taking the world by a storm. Just last month, the world was dealing with the WannaCrypt ransomware causing mayhem across the world. Yesterday, a new ransomware (some are now calling it a malware) has been driving businesses, users, and governments crazy. It's called Petya(NotPetya/SortaPetya/Petna).
What is Petya Ransomware?
First, what's a ransomware? Ransomware is a malicious piece of software that locks all the files on a computer. The only way to unlock them is after paying a ransom amount. Until then all files are encrypted and hence useless.
Petya has been in existence since 2016. This current ransomware is being called Petya because of it's close resemblance of the Petya that has existed before. It differs from typical ransomware as it doesn’t just encrypt files, it also overwrites and encrypts the master boot record (MBR). The Petya ransomware attacks networks through exploiting a security flaw in Microsoft's Windows operating system that was originally used by the National Security Agency (NSA). The vulnerability, known as EternalBlue, was leaked online earlier this year and is being used by hackers. The WannaCrypt ransomware that affected many businesses last month was based on the same security flaw.
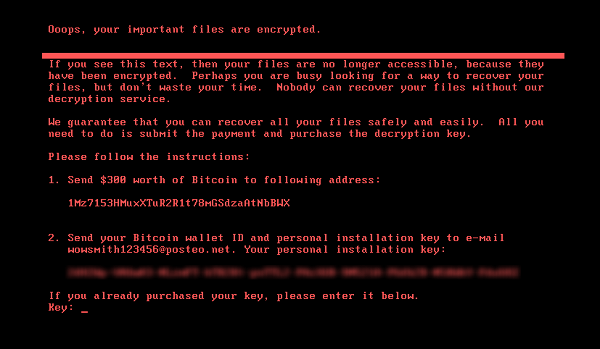
In this latest attack, the following ransom note is displayed on infected computers, demanding a payment of $300 worth of Bitcoins in order to recover the files:
How does Petya Spread?
There are numerous ways by which the notorious Petya ransomware can spread. Initially, it chooses two methods to infect PCs and only moves to the second method if the first one fails. And the first method is leveraging the leaked EternalBlue exploit which was initially discovered by the American security experts.
This method can fail if the system has been patched properly. In that case, it moves to the second method where it uses Windows administrative tools. Petya generally spreads to local networks first and limits its global impact in the early stages.
Some researchers have also found out that Petya can infect systems through watering hole attacks and phishing emails as well. In some cases, the ransomware was also associated with a Ukrainian tax accounting software MeDoc. The hackers bundled Petya to software updates associated with the product.
Who is affected by Petya Ransomware?
Petya ransomware was first in Ukraine. As per the latest reports, it has infected systems in Spain, Germany, Israel, the UK, Netherlands and the US. Major corporations have been affected including WPP, Maersk, Russian oil giant Rosneft, and public and private institutions in Ukraine. Even the Chernobyl nuclear reactor reported instances of Petya.
Microsoft estimates over 12,000 machines have been hit by the cyber attack. Major corporations have also been affected including WPP, Maersk, Russian oil giant Rosneft, and public and private institutions in Ukraine. Some of those businesses responded on Wednesday.
WPP issued a statement saying that they have taken necessary steps to contain the attack and normal operations have resumed. Many of the businesses under the WPP brand were affected but they are "experiencing no or minimal disruption."
Most businesses affected by this threat are still assessing the impact and taking emergency measures to contain the attack while further investigations continue.
Who is at risk?
As per most of the reports, so far only major businesses have been attacked. Anyone who is at the receiving end of this attack will know as the infected screen demanding $300 in Bitcoins will appear.
If your organization is running a vulnerable version of Windows that hasn't patched (updated with the latest fix) then your business could be at risk.
Good Read: Ransomware as a Service (RaaS) & Its Implications in 2021
Who is Impacted?
The good news is that Petya only infects Windows systems and can't harm Android, Mac and Linux devices. Even patched Windows computers with the latest installed updates are vulnerable to the Petya ransomware. Moreover, devices connected to VPNs are also at high risk and can be severely impacted by Petya.
How to protect yourself from Petya Ransomware?
Most of the major antivirus companies including Symantec, McAfee, and Kaspersky now claim that their software is updated and actively detects and protects against Petya infections. Here are a few things everyone can do as a precaution:
- Run Windows Update to get the latest software updates.
- Make sure you have an authentic antivirus software on your system.
- Run a thorough scan of your system and setup an auto scan function every few hours for the next few days.
- Back up important data on your computer so it can be recovered if it's held for ransom.
Additionally, organizations should:
- Update their Windows machines and apply the latest security patches.
- Backup all essential and sensitive data.
- Scan all outgoing and incoming emails for malicious attachments.
- Ensure anti-virus programs are up to date and conducting regular scans.
- Run regular vulnerability assessments and penetration tests on all your applications, networks and servers at least once a year. Better yet, set up a system for active monitoring.
Needless to say, don't pay the ransom! Even if you have been affected by Petya, there's no way to get the necessary keys to restore your documents. The email that is provided in this message has been shut down by the email service provider. Unless another email is up and running, this one is not going to help anyways. Hence, there's no point in paying the ransom.
Vaccine to prevent Petya Ransomware
Cyberreason's Principal Security Researcher, Amit Serper, was the first to discover that Petya would search for a local file and would exit its encryption routine if that file already existed on disk. His initial findings have been confirmed by other security researchers as well.
This means victims can create that file on their PCs, set it to read-only, and block the NotPetya ransomware from executing.
Please note that this is not a killswitch but rather like a vaccine. This is because each computer user needs to create this file independently.
How to Enable the NotPetya/Petna/Petya Vaccine
To vaccinate your computer to prevent being infected by Petya, simply create a file called perfc in the C:\Windows folder and make it read only. For those who want a quick and easy way to perform this task, Lawrence Abrams has created a batch file that performs this step for you.
Stay safe everyone! Make sure you take all the necessary precautions and be extra cautious on anything that might seem malicious. We'll keep updating this post as we know more about the latest developments.




 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Harshit Agarwal
Harshit Agarwal










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

