Cyber-attacks are on the rise..each day..every day. There are no two ways about it. We have said this time and again that Cybercrime is the greatest threat to every company in the world. And the key to winning against cybersecurity threats is to incorporate security proactively and religiously into their overall business process strategies. If you are looking to hire a security researcher with expertise in engineering secure systems and infrastructure, you can explore the Security Engineer job listings on RemoteWok. These professionals are well-versed in implementing security measures and developing robust solutions to protect your company's assets. Visit the Security Engineer job listings on RemoteWork.com to find qualified candidates for your team. One important aspect of developing a sound cybersecurity strategy is to hire a security researcher for your business.
Another crucial aspect of cybersecurity is vulnerability management. To ensure that your company stays proactive in identifying and addressing vulnerabilities, consider hiring a security researcher with expertise in Vulnerability Management. These professionals specialize in analyzing systems, networks, and applications to identify weaknesses and recommend remediation strategies. RemoteWokr offers a dedicated section for Remote Vulnerability Management job opportunities, allowing you to find skilled researchers who can help fortify your company's defenses.
Security researchers are cybersecurity advocates that attempt to counter the tsunami of cyber attacks by promoting security best practices and encouraging security technology adoption. They are responsible for conducting research and analysis of new vulnerabilities that are increasing day by day.
However, little is known about the skills necessary for successful cybersecurity advocacy. To hire a security researcher that is ideal and a rockstar for your company, you need to look out for someone with a broad set of skills to fulfill a wide spectrum of tasks of investigating an ecosystem with a constantly changing threat landscape. They must possess not only soft and technical skills but also context awareness and customer service orientation.
Hire Security Researcher. But Why?
If you think the above is an exaggeration, let the statistics ahead do the talking.
1,946,181,599: Total number of records containing personal and other sensitive data that have been in compromised between Jan. 1, 2017, and March 20, 2018
There's more to this than meets the eye. Here are some more shocking statistics to give you a sense of this ever-growing threat landscape and the need to hire the right cybersecurity advocates -
• Cybercrime damage costs to hit $6 trillion annually by 2021: 'Cybersecurity Ventures' predicts cybercrime damages will cost the world $6 trillion annually by 2021. Steve Morgan, Editor-In-Chief, believes that cybercriminal activity is one of the biggest challenges that humanity will face in the next two decades. The numbers do prove him right! (Source)
• Cybercrime would be more profitable than the global trade of all major illegal drugs combined: The above number is up from $3 trillion predicted in 2015, thus representing the greatest transfer of economic wealth in history, risking the incentives for innovation and investment, and as stated above, more profitable than the global trade of all major illegal drugs combined. (Source)
• Hackers smell blood now and not silicon as human attack surface to reach 6 billion people by 2022: As the world is going digital, humans have surpassed machines in becoming the number one target for cybercriminals. In 2017, there were 3.8 billion internet users which constituted around 51% of the world’s population of 7 billion. This number is predicted to increase up to 6 billion internet users by the year 2022 (which would be 75% of the projected world population of 8 billion). (Source)
• Global ransomware damage costs are predicted to exceed $5 billion in 2017: This is up from the $325 million that was predicted in 2015 - a 15X increment in just two years and the sad part is that things are being expected to get worse from here. Further, the ransomware attacks on healthcare organizations are expected to quadruple by 2020. Cybersecurity Ventures predict that the damage costs arising from ransomware attacks will rise to $11.5 billion in 2019 and that a business will fall victim to a ransomware attack every 14 seconds by that time. (Source)
From the above scenario, it is quite evident that our initial statement of 'Cybercrime' being the greatest threat holds true. And not just that..in the next five years, it might be the greatest threat to every person, place, and thing in the world.
The need of the hour for companies is to employ more and more cybersecurity advocates with the right skills and ability to promote best practices, educate, persuade, and serve as change agents for cybersecurity adoption. And the following tips will help you to hire the right person for the job.
Here's How You Can Hire A Rockstar Security Researcher
There are certain things to keep in mind on how businesses should go about hiring the right security researcher. For the purpose of this blog post, we are dividing the requirements into three categories. They are as follows:
1. Real-World Experience
Identifying vulnerabilities in a real-world attack scenario is one the most crucial requirement while hiring cybersecurity advocates. The candidate should have a history of exposure to real-world scenarios where they have evidence of finding security issues for any company. They should have either posted proof of those vulnerabilities on their personal blogs or participated in bug bounty hunting and reported the said issues to the company and are enlisted in their 'Hall of Fame'.
The validation here is that being equipped with the right cybersecurity certification is part of the theoretical aspect. Having a practical experience of finding real-life vulnerabilities is what that counts. As half of your work of finding a suitable candidate is already done when you one with such a practical experience.
2. Technical Skills
Cybersecurity is most often viewed from a technical perspective, with innovative technology and highly technical workers seen as the path to solving security problems. So it goes without saying that the right security researcher should possess a strong technical knowledge to gain credibility with their peers and
target audiences.
“This is a business that is very technology oriented, and full of people…who want to one-up you. So if you can’t kind of deal with that, it’s going to be hard for you to be an effective advocate because people will kind of eat you up unless you’re pretty convincing.” (Source)
Let's start with the basics first. For example - if we are hiring a security researcher at Appknox, we would be looking for someone who has the basic understanding of mobile security, how the mobile operating system works, basics of Android/iOS etc. Since Mobile Security is still in its infancy, it is important to hire someone who has the knowledge of the basic concepts in the mobile security ecosystem.
The next step would be to check the typical skills required for cybersecurity advocates. The top most common certifications are CISA, OWASP, CISSP, CISM, CRISC, CCIE, and CEH.
Further, you need to hire someone who has an innate curiosity about how software can be broken down or bypassed so you can do things with it that weren’t intended to be done.
"A person looking to move into security research has to be immersed in technology with a desire to understand the workings of malware, encryption, and network forensics and web applications because they are all intertwined. Plus, as a security researcher, you are not going do the same thing each day." - says Patrick Snyder, senior manager of AlienVault Labs.
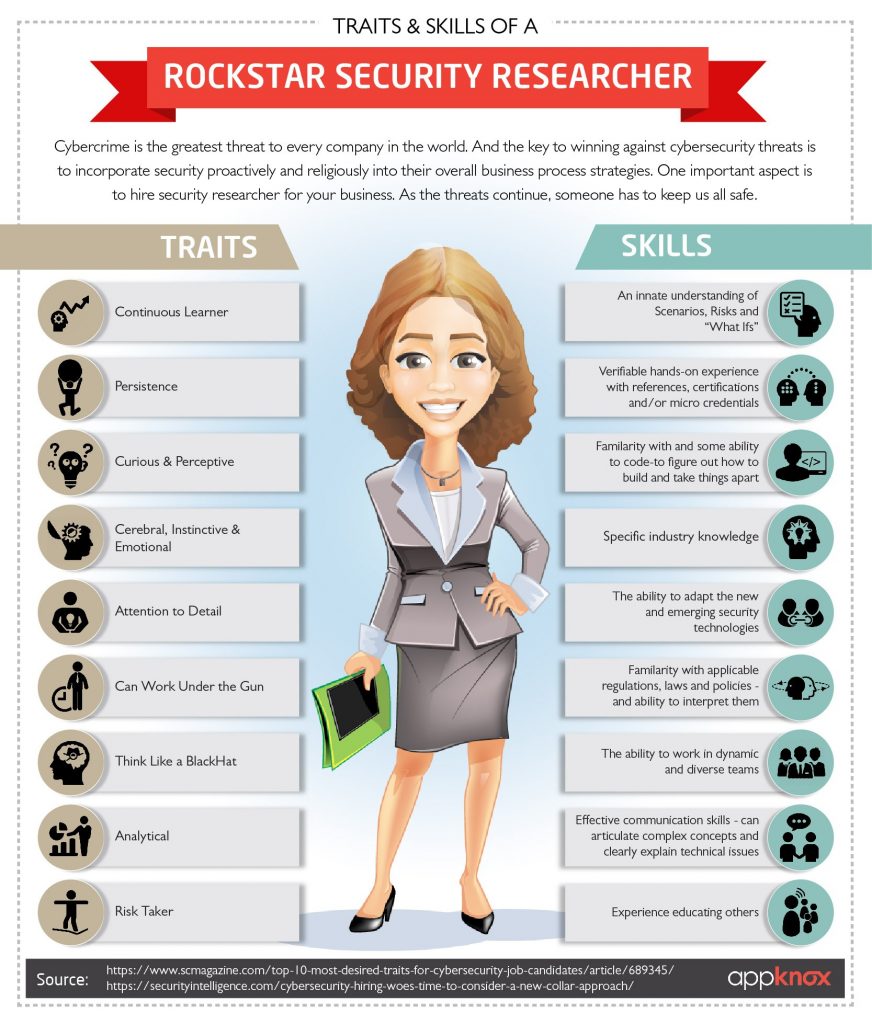
3. Soft Skills
Technical skills are important, but to be an effective cybersecurity advocate one needs to have a well-rounded approach towards addressing social and organizational factors other than the technical solutions alone.
“If you’re a computer scientist, and all you know is the computer science, and you don’t have the empathy, you don’t have the skills to listen,…you don’t have that psychological side, I don’t think you can make it work.”
These soft skills consist of personal attributes such as likeability and a positive attitude; career and collaborative attributes such as critical thinking, adaptability, and teamwork; people skills such as empathy and relationship building; and communication skills.
Final Thoughts
Last but not the least, there is a serious lack of good security talent around the world and companies are having a tough time hiring the best ones.
Cybercrime will more than triple the number of unfilled cybersecurity jobs, which is predicted to reach 3.5 million by 2021. Every IT position is also a cybersecurity position now. Every IT worker, every technology worker, needs to be involved with protecting and defending apps, data, devices, infrastructure and people. (Source)
If you are struggling to hire security researcher, Appknox is a perfect blend of automation and human security expertise to help you deliver the best security for your mobile apps, even if you have zero security resources on your team.
Our security reports are simple and easy to understand for all developers because we understand that not everyone might have a strong security background. Get in touch with us today to know more.




.jpg)
 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Harshit Agarwal
Harshit Agarwal










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

