An increase in DDoS attacks was one of the popular cybersecurity predictions last year. With the growth of the sharing economy, we've definitely seen an increase in the number as well as the damage caused. In fact, we've got a lot of our customers asking if DDoS attacks on mobile apps are possible. The short answer is definitely yes. But this post is to understand how these attacks on mobile apps work and how you can be safe.
Let's start with some basics.
|
What is a DDoS Attack Meaning?
Distributed Denial of Service attack is a type of cyber attack where multiple computers or devices usually infected with malware act as a network of bots and attack a server to make it unusable.
DDoS Attacks on Mobile Apps?
Mobile apps, in general, are a threat to these dreaded attacks. In fact, mobile apps have been used to control mobile devices that are used to perform such attacks as well.
One of the reasons why mobile apps are susceptible to these attacks is because it is easy for an attacker to profile the user itself and that tremendously increases the probability to be able to perform DDoS attacks on mobile apps in a successful manner.
Many social and sharing apps like Facebook, Linkedin, Instagram, Uber, Ola, Airbnb, etc. are all susceptible to such attacks because it is easier to profile individual users through their mobile devices. Another thing about mobile application security is that more often than not they aren't very well secured.
We've done a detailed report on security issues in banking apps and a report on security issues in m-commerce apps and have found more than 80% of apps in both cases to be weak in security. Remember, all these apps have transactions and money involved and the expectation for security is way higher.
What does a DDoS attack on Android apps look like?
Well, if we take a really simple example then imagine someone built an app and put it on the mobile app store, and you as a user downloaded this app. This app itself can either expose you to a DDoS attack or open up some new security loopholes on your mobile device so that it can be used for such an attack on some other server.
This basically means the attacker has control of your device via the app that they built and you downloaded. This way, you can either be a victim of a DDoS attack or a source. Neither is a good sign.
DDoS attacks cause a lot of direct damage especially to companies since it blocks web traffic leading to reduced revenue, and also adding to a high cost in terms of remediation. Additionally, there's always the threat of losing the customer's trust which you've built over the years.
Common DDoS Attack Types
Let us take a look at some of the standard attack types when it comes to DDoS attacks:
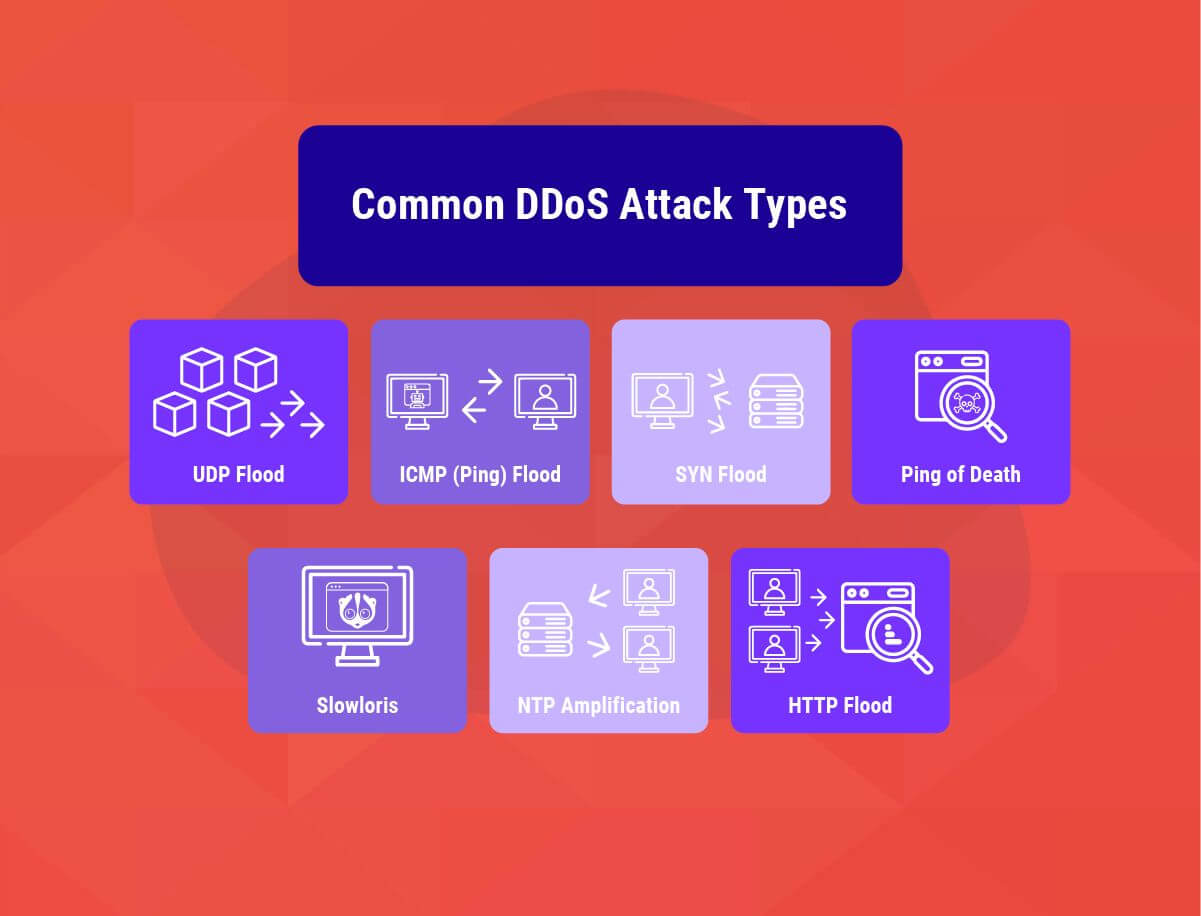
1. UDP Flood:
A UDP flood can be defined as a DDoS attack that floods random ports on remote targets with UDP (User Datagram Protocol) packets. This makes the host continuously look out for the application associated with these datagrams, and (when no such application is found) respond with the help of a ‘Destination Unreachable’ packet. This entire mechanism saps host resources and can ultimately lead to inaccessibility on the part of the user.
2. ICMP (Ping) Flood:
Based on a similar principle as that of the UDP flood attack, the ICMP or ping flood attack targets resources with ICMP Echo Request (ping) packets. This attack mainly focuses on pushing the packets as fast as possible without caring for replies. Both incoming and outgoing bandwidths are affected by this attack. The overall system further slows down as the victim’s servers also start responding with ICMP Echo Reply packets.
3. SYN Flood:
In the case of an SYN flood DDoS attack, a known vulnerability in the TCP connection sequence (the “three-way handshake”) is exploited. In the SYN flood attack scenario, multiple SYN requests are sent by the requester, but none of them responds to the host’s SYN-ACK or dispatches the SYN requests from a spoofed IP address. In either of the cases, the host system keeps on waiting for acknowledgment for any of the requests. This continues until no new connections can be made and this ultimately results in the denial of service.
4. Ping of Death:
In the case of the Ping of Death DDoS attack, an attacker bombards a target computer with a series of contorted or malicious pings. The general maximum length of an IP packet is around 65,535 bytes. But the Data Link Layer on the networks poses certain limits on the size of packets. In such a scenario, these packets are further split into multiple smaller packets and are later reassembled by the beneficiary host into complete packets of the required size. However, under an attack scenario, recipients receive IP packets of larger sizes which overflow their memory buffers. This ultimately results in the denial of service for authentic packet requests.
5. Slowloris:
One of the most highly-dreaded DDoS attacks, Slowloris prepares one web server to take down another target server without affecting other services or ports on the destined network. Slowloris makes this possible by keeping multiple connections to the target web server open for as long as desired. Slowloris continuously sends multiple HTTP headers but never completes the requests. The unaware target server keeps these false connections open and waits for their completion. This eventually results in overflowing the maximum concurrent connection pool and further leads to the denial of legitimate connections from actual consumers.
6. NTP Amplification:
In the case of NTP amplification attacks, publicly accessible Network Time Protocol (NTP) servers are exploited by attackers. In this attack, the threat actors target servers by overwhelming them with UDP traffic. This attack is generally described as an amplification attack because its query-to-response ratio generally varies in the high range between 1:20 and 1:200 and even more. This further implies that an attacker can easily generate a devastating high-bandwidth, high-volume DDoS attack once he obtains a list of open NTP servers (by using data from the Open NTP Project or by utilizing devices like Metasploit).
7. HTTP Flood:
In the case of an HTTP flood DDoS attack, an attacker exploits seemingly authentic HTTP POST or GET requests in order to attack applications and web servers. Dependence on malicious packets, web spoofing, or other reflection techniques usually doesn’t happen during an HTTP flood attack. Moreover, less network bandwidth than other attacks is required to bring down the targeted site or server.
The attack is most dangerous when it forces the target server or application to designate the maximum resources possible in return for every single request.
3 Types of Mobile Apps DDoS Attacks
DDoS attacks can be categorized into three major types. However, irrespective of the type of attack, the end goal of the threat actors is always the same: to make the target resources unresponsive and sluggish. Let’s see how these three types of attacks usually unfold:
1. Volume-Based DDoS Attacks:
These attacks aim at saturating the bandwidth of the target websites or servers by overwhelming them with massive volumes of bogus traffic. ICMP floods, UDP floods, and other spoofed-packet flood attacks come under the category of volume-based attacks.
2. Protocol or Network-Layer DDoS Attacks:
The protocol or network-layer attacks consume the resources of the target infrastructure tools by sending large amounts of spoofed packets. Generally measured in PPS (Packets Per Second), these attacks include Ping of Death attacks, SYN floods, and Smurf DDoS attacks among others.
3. Application-Layer DDoS Attacks:
The application layer attacks involve overwhelming applications by flooding them with malicious code requests. These requests seem to be legitimate only at the first sight, but they eventually crash the entire web server and cause a denial of service.
These attacks involve slow and low-level attacks like POST or GET floods and generally target Windows, Apache, and OpenBSD vulnerabilities. The size of these attacks is measured in RPS (Requests Per Second).
Numerous Apps Used to Launch DDoS Attack from Play Store
The WireX botnet (a collection of internet-connected devices) recently cause havoc around the world and disrupted many popular services. This was one of the first and biggest DDoS attacks on Android systems. This botnet was hidden within some 300 apps which were available officially on the Google Play Store.
When users installed the app, WireX added individual mobile devices into a larger network which was then used to send junk traffic to certain websites in an effort to bring them down and make them unusable.
Google has removed roughly 300 apps from its Play Store after security researchers from several internet infrastructure companies discovered that the seemingly harmless apps—offering video players and ringtones, among other features—were secretly hijacking Android devices to provide traffic for large-scale distributed denial of service (DDoS) attacks.
Another large attack that caught everyone's attention last year was the Mirai botnet, which crippled the Internet and brought down sites such as Amazon, Github, PayPal, Reddit, and Twitter.
Related Topic- Man in the Middle Attack ( MITM ) on Mobile Applications

Features of DDoS Attacks on Mobile Apps
Some of the common features of DDoS attacks involving mobile devices and mobile apps are as follows:
- Most of these attacks involve both Android (60 percent) and iOS (40 percent) devices almost equally.
- Attackers generally initiate attacks with a large number of mobile devices. In a typical attack, the number of mobile devices may reach half a million and the number of requests per second (QPS) can reach up to millions. Moreover, it's difficult to track their IP address as well.
- Attackers generally use source IP addresses which are widely distributed across hundreds of countries all over the world.
- It has been observed that the DDoS attacks involving mobile apps use cellular base stations as their gateway IP addresses. These stations handle both user traffic as well as attack traffic.
In typical DDoS attacks, the attack duration and the attack frequency of the attack source IP address vary according to the target mobile app and device configuration.
How are Attacks Involving Malicious Apps Initiated by Hackers?
Hackers follow a series of steps in order to initiate DDoS attacks involving malicious apps.
- At first, WebView is embedded by hackers into apps, and the central control link is requested. The link redirects to a page that is embedded with JavaScript files in order to obtain JSON instructions.
- In case no attack is initiated, the JSON instruction reads - {"message": "no data", "code": 404}. The instructions are read periodically by pushing the JavaScript files into a continuous loop.
- When attack-type instructions are passed, the JavaScript files exit the continuous loop, and JSON instructions are parsed. The JSON instructions carry all the necessary details which are required for the attack like the packet content, header, request method, and target URL, and also specify parameters like attack start time, attack end time, frequency of attack, and so on.
- After this, WebView finds out the operating system of the devices using UserAgent. Later, WebView triggers the loading of Java code into a malicious app using different functions for different device types. Subsequently, based on the JSON instructions, an attack is initiated.
Once these techniques are followed and the users install such fraudulent apps, hackers could successfully initiate DDoS attacks targeted at desired institutions and businesses. Using deceptive ads, the owners of these malicious apps attract users to install these apps.
These fraudulent apps can not only control mobile devices for initiating DDoS attacks but also access sensitive user data like location, bank accounts, contacts, and whatnot. All of this can also result in identity theft and telecommunication fraud.
Prevent DDoS Attacks on Mobile Apps
So, what can you do to prevent DDos attacks? These rules apply to all mobile users, irrespective of whether it is for personal or enterprise use. Needless to say, it's even more important for enterprises because of the impact of the damage these attacks can cause.
1. Think Twice, Always:
Sometimes an app might sound like it's too good to be true. It's always good to look at it with some skepticism. Before you go ahead and download the app, make sure you read some reviews, check the ratings, and even do a quick Google Search to know if there's some history with this app that might be troubling.
2. Stay Updated:
Always ensure your mobile operating system, as well as the apps on it, are regularly updated. Manufacturers and platforms and app developers work with security companies to identify security issues and push critical updates that solve these security bugs. You won't benefit unless you update the app.
3. Choose Wisely:
Always search a little more for the apps that you need for a particular purpose. If you see an app with bad reviews and ratings, a deeper search can help you find other apps with the same purpose but better.
4. Perform Security Audits:
Try to establish different layers of security in your perimeter. As an enterprise, you can take advantage of the variety of sophisticated mobile app security solution providers to help with your security needs. As an individual user as well, ensure you have anti-malware apps on your mobile devices to help you detect any abnormalities.
With the vast amount of data flowing through the sharing economy, these apps are without a doubt a prime target for attackers - sometimes for ransom and sometimes just to disrupt services or exploit the personal data of millions of users.
Make sure you are aware of all the security risks. Ensure the same awareness for your employees as well as customers.
How can we Cope Up with DDoS Attacks?
It becomes really difficult to defend security systems when a massive number of mobile devices become sources of DDoS attacks.
Following traditional methods like blacklisting and rate-limiting doesn’t help and organizations have to come up with more innovative methods of security. Some of the measures which can help mitigate these threats are:
- Identification techniques of attack traffic must be extended. Each server request should be tested in real-time on a multi-dimensional testing platform.
- Steps must be taken to filter out attack traffic by organically combining various dimensions like intelligent identification techniques, imposing fines, and making the control unit more flexible.
- In order to reduce the impact on business and improve the speed of response, organizations must replace artificial troubleshooting with other techniques like machine intelligence.




.jpg)
 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Abhinav Vasisth
Abhinav Vasisth










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

