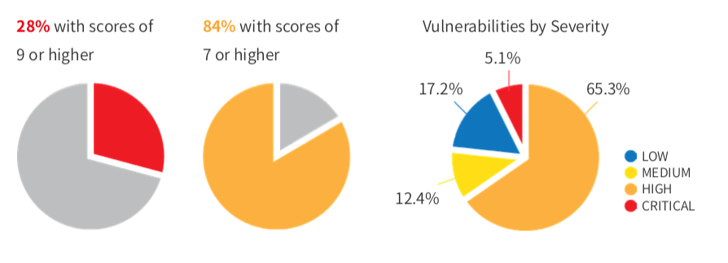
Appknox and SEWORKS have together published an m-commerce security report showcasing the security trends in the top 50 mobile apps in the shopping category in the US. Our findings show that over 84% of the apps analyzed have more than three high-level vulnerabilities in them.
The shopping category on the app store is one of the most popular in terms of downloads and activity. With growing access to smartphones and reliable internet around the world, there are only more people jumping onto the e-commerce and m-commerce wave. But are they secure?
Why an M-Commerce Security Report?
The idea behind conducting this research was to generate awareness that many popular mobile apps built today are plagued by security issues and vulnerabilities. We chose the shopping category because this is one of the categories with the most downloaded apps that also involve numerous financial transactions on a daily basis. It’s important for businesses to become proactive and perform a security check before launching mobile apps. This report is an attempt to encourage a step in that direction.
The mobile shopping experience is becoming extremely convenient with options to store the consumer’s credit card and shipping address information. Oftentimes, shoppers simply need to click on the purchase button on an app to complete their shopping, without entering any additional information. However, do those apps have sufficient security measures? That’s the key question we wanted to ask and that is what our report helps answer.
Key Findings from the Mobile Commerce Security
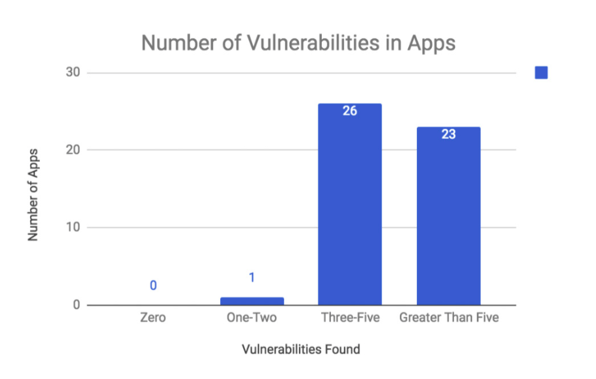
A total of 274 vulnerabilities were detected among the top 50 Android mobile shopping apps, and all had security risks. The apps were tested across 34 different security testing categories.
94% of the apps failed an “Unprotected Exported Receivers” test. Android apps export receivers, which respond to external broadcast announcements and communicate with other apps. For instance, when Receivers are not protected — hackers can modify the app’s behavior as they wish, and insert data that doesn’t belong to the apps.
70% of the apps were found to be affected by “Unprotected Exported Activities.” Activities are executed via authorized access. When an Activity is exported with no protection, it can be remotely launched outside of the app. This may allow hackers to access sensitive information, modify the internal structure of the applications, or deceive a user into communicating with the compromised application while believing they are still interacting with the original application.
64% of the apps were affected by “App Extending WebView Client.” When WebView Clients are not correctly protected by in-app extensions, hackers can deceive users into inputting sensitive personal information into fake or copied apps, resulting in loss of user data, damages, and SSL compromises.
The complete list of security vulnerabilities can be found in the Appknox and SEWORKS report, the m-commerce security report for the USA.



 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Prateek Panda
Prateek Panda










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

