For more than a decade, cyber security has been a concern for the government and private sector alike. The growth in Information Technology and E-commerce sector in the United States has given rise to cyber crimes, causing a huge loss to the US government and its people. Today we have a glance at the United States cyber security laws and regulations.
Data breaches have gained more attention due to the impact of digitization on financial, healthcare, SMEs, and other industries. Even though data breaches occurred way before digitization took the world by storm, the popularity of digital platforms gave a new dimension to these breaches as the importance, volume, and cost of the data breaches have increased considerably.
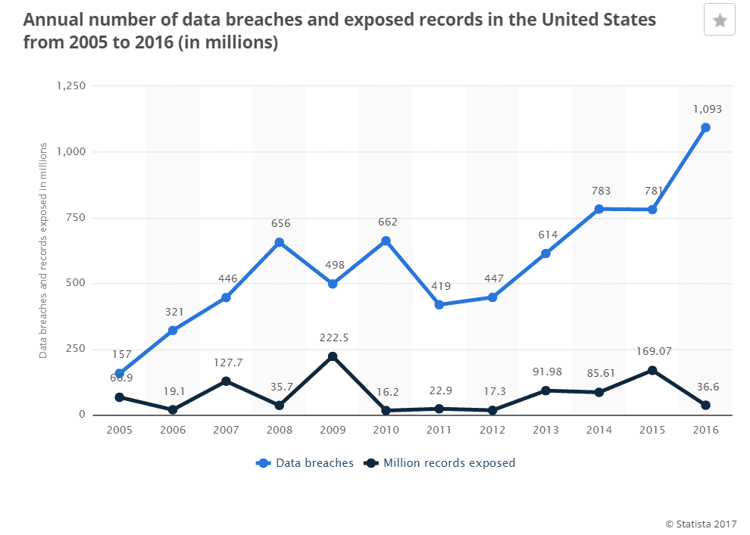
The number of data breaches in the U.S. increased from 157 million in 2005 to 781 million in 2015, while the number of exposed records jumped from around 67 million to 169 million during the same time frame. In 2016, the number of data breaches in the United States amounted to 1093 with close to 36.6 million records exposed.
The year 2016 witnessed the largest data breach to date in US history as the online platform Yahoo revealed that hackers stole user data and information related to at least 500 million accounts back in 2014. In December 2016, the company announced another hack dating back to 2013 that affected over 1 billion user records.
Consumer Privacy Protection Act of 2017
The Consumer Privacy Protection Act of 2017 aims at securing the personal information of customers, avoid identity theft, update citizens and organizations regarding security breaches, and prevent the misuse of sensitive user information.
The act is applicable to all the institutions which access, collect, store, use, and transmit personally identifiable information of more than 10,000 US citizens over a specified period of time. The associated penalties and fines do not exceed more than $5 million. But, if it is found that the misuse of data was intentional, an additional $5 million fine can also be imposed.
Understanding the United States Cyber Security Laws and Regulation
The United States cyber security laws and privacy system is arguably the oldest, most robust, and most effective in the world. The State's’ privacy system relies more on post hoc government enforcement and private litigation. Currently, cyber security regulation comprises directives from the Executive Branch and legislation from Congress that safeguards information technology and computer systems.
The purpose of cyber security regulation is to force companies and organizations to protect their systems and information from cyber-attacks such as viruses, trojan horses, phishing attacks, denial of service (DOS) attacks, unauthorized access (stealing intellectual property or confidential information), and control system attacks.
.webp?width=750&name=United-States-Cyber-Security-Laws-1%20(1).webp)
Federal Government Regulation
There are three main federal cybersecurity regulations -
- 1996 Health Insurance Portability and Accountability Act (HIPAA)
- 1999 Gramm-Leach-Bliley Act
- 2002 Homeland Security Act, which included the Federal Information Security Management Act (FISMA)
These three regulations mandate that healthcare organizations, financial institutions, and federal agencies should protect their systems and information. However, these rules are not foolproof in securing the data and require only a “reasonable” level of security.
For example, FISMA, which applies to every government agency, “requires the development and implementation of mandatory policies, principles, standards, and guidelines on information security”.
But, these regulations do not address numerous computer-related industries, such as Internet Service Providers (ISPs) and software companies. Furthermore, the vague language of these regulations leaves much room for interpretation.
“Bruce Schneier, founder of Cupertino’s Counterpane Internet Security, argues that companies will not make sufficient investments in cybersecurity unless government forces them to do so. He also states that successful cyber-attacks on government systems still occur despite government efforts.”
Recent Federal Laws
In a recent effort to strengthen its cyber security laws, the federal government is introducing several new cyber security laws as well as amending the older ones for a better security ecosystem. Below are a few of them:
1. Cybersecurity Information Sharing Act (CISA)
Its objective is to improve cybersecurity in the United States through enhanced sharing of information about cybersecurity threats, and for other purposes. The law allows the sharing of Internet traffic information between the U.S. government and technology and manufacturing companies. The bill was introduced in the U.S. Senate on July 10, 2014, and passed in the Senate on October 27, 2015
2. Cybersecurity Enhancement Act of 2014:
It was signed into law on December 18, 2014. It provides an ongoing, voluntary public-private partnership to improve cybersecurity and strengthen cybersecurity research and development, workforce development and education, and public awareness and preparedness.
3. Federal Exchange Data Breach Notification Act of 2015:
This bill requires a health insurance exchange to notify each individual whose personal information is known to have been acquired or accessed as a result of a breach of security of any system maintained by the exchange as soon as possible but not later than 60 days after discovery of the breach.
4. National Cybersecurity Protection Advancement Act of 2015:
This law amends the Homeland Security Act of 2002 to allow the Department of Homeland Security's (DHS's) national cyber security and communications integration center (NCCIC) to include tribal governments, information sharing, and analysis centers, and private entities among its non-federal representatives.
State Laws
State governments also have taken sincere measures to improve cyber security by increasing public visibility of firms with weak security. In 2003, California passed the Notice of Security Breach Act which requires that any company that maintains the personal information of California citizens and has a security breach, must disclose the details of the event. The security breach regulation regulations punish firms for their cyber security failures while giving them the freedom to choose how to secure their systems.
This regulation creates an incentive for companies to proactively invest in cyber security to avoid potential loss of reputation and economic loss. This worked well for California and later several other states that implemented similar security breach notification regulations.
Cyber Security Laws of New York
The financial services industry is a significant target of cyber security threats. Over the past few years, the New York State Department of Financial Services (“DFS”) has been closely monitoring the ever-growing threat posed to information and financial systems by nation-states, terrorist organizations, and independent criminal actors.
Cybercriminals of late have sought to exploit technological vulnerabilities to gain access to sensitive electronic data. These criminals can cause significant financial losses for DFS-regulated entities as well as for New York consumers whose private information may be revealed and/or stolen for illicit purposes.
Given the seriousness of the issue and the risk to all regulated entities, certain regulatory minimum standards are warranted, while not being overly prescriptive so that cyber security programs can match the relevant risks and keep pace with technological advances.
Accordingly, this regulation is designed to promote the protection of customer information as well as the information technology systems of regulated entities. This regulation requires each company to assess its specific risk profile and design a program that addresses its risks in a robust fashion.
The New York Cyber Security regulation has been effective since March 1, 2017. Covered Entities will be required to annually prepare and submit to the superintendent a Certification of Compliance with New York State Department of Financial Services Cybersecurity Regulations commencing February 15, 2018.
Final thoughts
Going by the looks of the United States cyber security laws and regulations above, it is pretty evident that the government has been working to introduce stricter laws to equip organizations to secure their data from the latest cyber threats. However, Bruce Schneier rightly said that successful cyber-attacks on government systems still occur despite government efforts. This holds true for private companies as well.
It is advisable that organizations become proactive about the security of their apps and data. Cybercriminals are always on the prowl & are becoming sophisticated in their approach to attack. For the same reason, companies should keep a regular check on their systems to identify any vulnerabilities and address the loopholes immediately.
Related Posts
A Glance At Australia’s Cyber Security Laws
A Glance At Singapore Cyber Security Laws




.jpg)
 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Harshit Agarwal
Harshit Agarwal










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

