The rapid evolution of the world of smartphones and mobile applications has skipped no one's eyes. Around the globe, around 5.19 billion people now use smartphones and almost 90% of their time is spent on mobile apps. The fact that a major chunk of the human populace relies on smartphones and mobile apps to store their personal and financial information makes matters pretty serious. McAfee reported a 30% increase in the number of malicious apps which led to more than half of the mobile security threats in recent years.
The challenges of safeguarding consumer and business data are now even bigger and that is why it becomes essential to follow some of the established best practices for mobile application security.
Why is Mobile Application Security a Big Deal?
To understand why this is a big deal, we need to take a more holistic view. Let's scale this up. There are many reports out there that have proven that more than 90% of mobile applications are vulnerable and there's a median of around 6.5 vulnerabilities per app.
At the same time, over 4,000 apps are being added to the popular app stores every single day. On average, a smartphone user downloads 36 apps. Put this all together and it will present a scary picture for any business.
Why do Companies need to Focus on Application Security Practices?
At the speed with which enterprises are becoming victims of cyberattacks, application security is necessary if not mandatory. Here are a few reasons why your business should prioritize application security:
1. Enhanced Customer Trust and Market Reputation
In today’s cybersecurity threat landscape, more and more companies are becoming victims of data breaches, often struggling to survive in the industry later on. However, businesses that strictly follow basic security measures like mobile application security are less likely to fall prey to cyberattacks. This, in turn, helps maintain a sound market reputation, which is a key driver for the growth of your business.
2. Saves Time and Resources
Saving money on cybersecurity breaches by enforcing better application security protocols can reap long-term profits. Remember, a single code injection attack is enough to expose the data records of thousands of customers and clients.
With best practices, you can detect vulnerabilities early in the SDLC process, thereby exposing security risks that might pose severe threats in the future. By quickly detecting vulnerabilities, you can mitigate them early in the development stages, and save a lot of time and resources.
3. In Order to Meet Security Compliance and Regulations
For apps that deal with the sensitive information of users, application security is extremely important. It helps you comply with security standards and regulations such as HIPAA, PCI-DSS, etc. that might be mandated by cybersecurity law.
Further, if your organization does not comply with the security guidelines, you might be subject to hefty fines and fees. To avoid paying heavy charges due to non-compliance and maintain better security, consider implementing application security.
Good Read: Compliance Checks That Businesses Need To Follow
5 Essential Mobile Application Security Best Practices For Companies
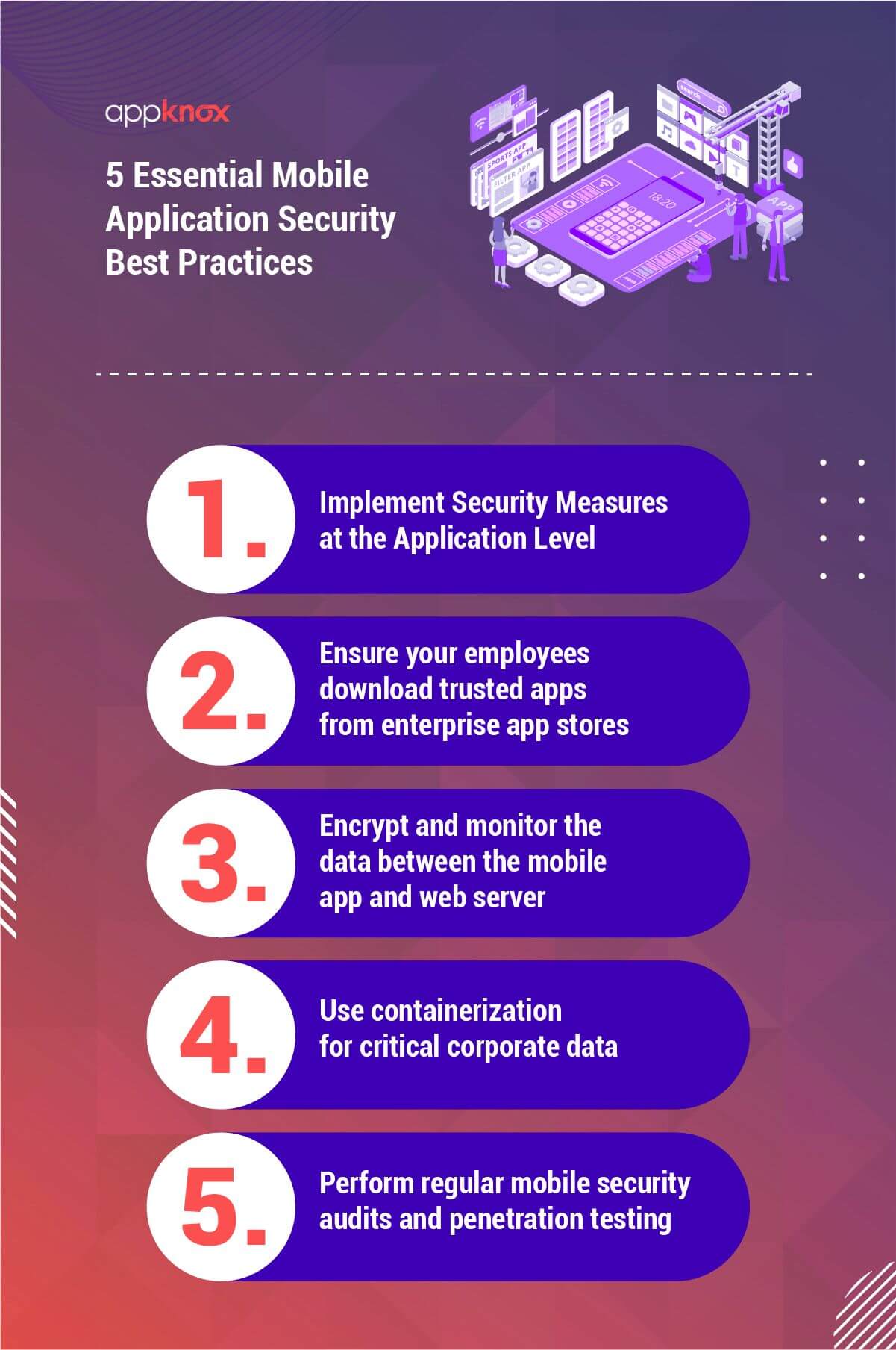
1. Implement security measures at the application level
Device manufacturers and operating systems will keep implementing some or the other security measures from time to time. Relying on them to make you secure is a terribly wrong expectation. Many businesses and developers believe that being on the iOS platform makes them secure.
Although I agree iOS is fairly better in terms of security compared to Android, that is changing. Hence, as a business, you should make sure you take care of mobile security at the application level which will reduce your dependency on platforms and devices to keep you safe and secure.
2. Ensure your employees download trusted apps from enterprise app stores
Although this method is not 100% foolproof, yet it is one of the biggest mistakes companies make. Enterprises should make it a rule of thumb to not trust third-party applications at all unless pre-approved through a security testing process.
While you employ BYOD principles at work, it is important to educate your employees on the security risks involved in downloading and using apps that come from third-party sources. For all internal apps, create a safe and secure enterprise app store allowing employees to have access to these apps.
3. Encrypt and monitor the data between the mobile app and web server
It is important to sometimes manually analyze the traffic flowing through the app to the web servers. You can either have an internal team to do that or hire a mobile app security company that can help you track movements in the network layer.
Most experts will recommend all mobile device communications be encrypted. The reason is simply that wireless communications are quite easy to intercept and snoop on. Often known as the transport layer, the path between the mobile app and web servers carries very sensitive information and it is necessary to employ the best security practices to make sure this is something you can monitor well.
4. Use containerization for critical corporate data
A good way to try and protect sensitive corporate information is a concept called containerization. The name itself is self-explanatory and means that you can use techniques to store sensitive corporate data into a separate container in the mobile app.
This is a good way to employ a system that identifies your corporate data as more sensitive as compared to say your selfies from the last vacation.
5. Perform regular mobile security audits and penetration testing
It is recommended that companies and organizations should hire a trustworthy and reputed mobile app security testing company to audit their applications at least once every quarter. Putting your mobile apps through a set of automated and manual penetration tests that follows the mobile application security best practices can be very helpful in deciding what aspects of security you need to focus on.
After identifying issues, it is even more essential to spend time with remediation and mitigation of any issues that were discovered. Even if you have an internal security team, it is always a good practice to get an external audit done as well.
Impacts of Weak Mobile App Security
Almost all contemporary apps store and use user credentials, bank information, and other PII (Personally Identifiable Information) to provide an enhanced user experience. However, with the advent of complex security threats, it has become difficult to maintain the required level of security. Let’s take a look at some of the impacts of weak mobile app security:
1. Reverse Engineering
Reverse engineering can be used to determine how the app functions on the back end, modify the source code, expose encryption algorithms in place, and more. So the code you developed for your mobile app can be used against you and pose severe security risks.
2. Insecure Data Storage
One major impact of ignoring mobile application security is the threat that arises when an adversary can access insecure data stored in a mobile device. An adversary can either gain physical access to a stolen device or enter it using malware or a repackaged app.
In the case of physical access to the device, the device’s file system can be accessed after attaching it to a computer. Many freely available software allows the adversary to access third-party application directories and the personally identifiable data contained in them.
3. Malicious Code Injection
Client-side injection or code injection results in the execution of malicious code on the mobile device via the mobile app. Typically, this malicious code is provided in the form of data that the threat agent inputs to the mobile app through a number of different means. The data is malformed and is processed (like all other data) by the underlying frameworks supporting the mobile app.
4. Unauthorized Access to your API
This problem occurs when a mobile device fails to recognize the user correctly and allows an adversary to log into the app with default credentials. This typically happens when an attacker fakes or bypasses the authentication protocols, which are either missing or poorly implemented, and interacts directly with the server using either malware that sits in the mobile device or botnets, thus establishing no direct communication with the app.
5. Confidential Data Theft
Sensitive data is any information that’s meant to be protected against unauthorized access. Data exposure happens when data is left unencrypted in a database or server accessible to anyone. When this data is accessed by an attacker as a result of a data breach, users are in danger of sensitive data exposure. Data breaches that end in the exposure of sensitive credentials can include costs within the millions of dollars, destroying a company’s reputation.
Top 3 Tools for Organization Mobile App Security
Here are some of the best mobile app security tools for your organization:
1. Appknox:
Appknox is considered one of the most reliable market solutions for Penetration Testing attempts to identify insecure business logic, security setting vulnerabilities, or other weaknesses that a threat actor could exploit. Critical factors like transmission of unencrypted passwords or password reuse are checked in real time with the advanced Appknox penetration testing solutions.
2. Zed Attack Proxy:
The OWASP ZAP (Zed Attack proxy) is one of the world’s most popular mobile app security testing tools that are free to use and is actively maintained by hundreds of volunteers worldwide. OWASP ZAP helps in finding security vulnerabilities automatically in applications during the development and testing phase. It's also a great tool for pen testers who are experienced enough to use it for manual security testing.
3. ImmuniWeb:
ImmuniWeb® MobileSuite offers a unique combination of mobile app and its backend testing in a consolidated offer. It comprehensively covers Mobile OWASP Top 10 for the mobile app and SANS Top 25 and PCI DSS 6.5.1-10 for the backend. It comes with flexible, pay-as-you-go packages equipped with a zero false-positives SLA and money-back guarantee for one single false-positive! ImmuniWeb® MobileSuite offers a free online mobile scanner for developers and SMEs, to detect privacy issues, verify application permissions and run holistic DAST/SAST testing for OWASP Mobile Top 10.




.jpg)
 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Abhinav Vasisth
Abhinav Vasisth










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

