In today's world of advanced technology, we hear about NFC quite often. I am sure most people keep having something about NFC in their newsfeed every once in a while. Major popular businesses are incorporating NFC-based technologies to simplify lives of consumers. While that is happening, it is essential to understand why NFC could also be the next big fraud vector. Before we get to that, let's understand NFC a little more.
What is NFC?
NFC or Near Field Communication is a set of standards or protocols to communicate between two devices by either touching or bringing into close proximity ( less than 4 cm ).
The communicating protocols of such devices are based on RFID Standards, including ISO 14443. These standards are defined and extended by the NFC Forum, which was founded on 2004 by some major companies such as Sony, Nokia, Philips, Samsung etc.
The operating Frequency of such communication is merely 13.56 MHz ( +/- 7 ) which is very low. This gives an advantage of easily integrating into portable devices without the need of much battery power.
Types of Communication in NFC-based devices
There are basically two types of communication possible in NFC-based devices:
1. Passive: In this type of communication unpowered NFC “tags” can be read using NFC-enabled devices. The initiator, that is the NFC device provides power to the “tag” which re-transmits back with the recorded data.
2. Active: In this type of communication, both devices simulates power to transmit data between each other. It can be more or less generalized as a Peer-to-Peer (P2P) transmission. In this way, binary/multimedia files can be transmitted with ease.
How is NFC Useful?
Using NFC-enabled smartphones, consumers can replace their credit and debit cards with an electronic wallet. Besides facilitating payments, NFC also has a wide variety of applications that it can be used for like:
- Access: Electronic identity & Physical Access control
- Transactions: Store Transportation passes, Electronic Payments
- Information: Store Personal information, View Product information, Receive discounts, Swap Media
(Must Read: Top 5 Risks In Mobile Payments That Can Cost A Fortune To Businesses)
Why is NFC the Next Big Fraud Vector?
At a 2012 BlackHat conference, a security researcher presented his findings on how he hacked many devices thus taking advantage of a variety of exploits. There is enough evidence now to show that NFC can be manipulated if considering that you have sufficient know-how.
Here are three real examples that make NFC the next big fraud vector:
1. ATM Card Skimmers
In countries where ATM cards are NFC enabled, the ATM cards could be used to complete transactions using the NFC functionality. So once the card gets in contact with the NFC card reader, the card reader retrieves some of the information from the card and uses it to complete the payment.
What an attacker could do in this scenario, is install his custom NFC-enabled card reader in any of the ATMs, which accept NFC-enabled credit cards. So, once the user goes to the ATM and uses the NFC-enabled ATM card, the attacker’s card reader would retrieve the information, and then pass it to the original card reader machine. So, this could be seen as an example of Man in the Middle Attack. Also, at the end of the day, the attacker could come to the ATM Machine, and take away his installed card reader, and get the information of all the cards used on that ATM on that day. He could then further use those card information, to perform malicious transactions and other activities.
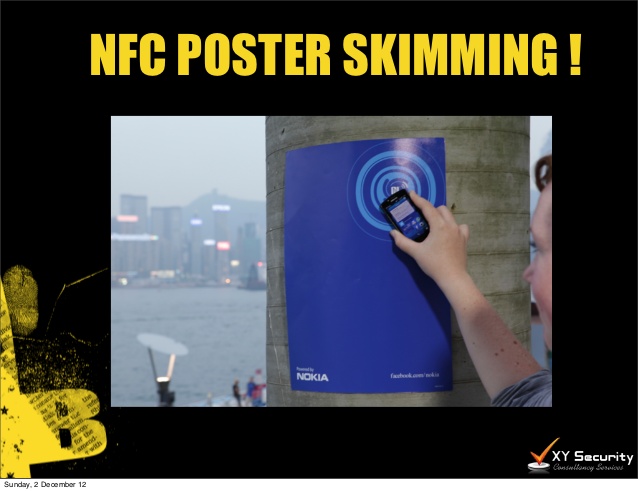
2. NFC Poster Skimming
Another attack vector using NFC could be seen regarding the NFC-based posters. The posters are used to provide advertisements where when an NFC-enabled device is tapped to the specified location in the poster the information is transferred, for example, we came across an NFC-enabled poster advertising a newly released track by a famous artist in Chicago International Airport. While tapping my GalaxyS3 with that poster, I got redirected to a signup form, upon completion I was able to download the trailer of the music video.A phone is a place where most of our private information is stored, an attacker can use this poster to transmit applications to your device thus compromising security.
3. NFC Relay Attack
This dangerous form of attack compromises the security of all organizations depending upon NFC cards as a proof of identification of customers or employees. An arbitrary example is the company provided id card which we use to get access to the building , an active device can read and copy the data from the passive cards and store it, thereby becoming a clone of the card, now instead of swiping the card, we can swipe the phone containing the data ACCESS GRANTED! This was the companies security at risk, now on personal security, an NFC enable credit or debit card will cause enough damage, imagine even without stealing the card from the user data will get transferred whenever an active device is close enough. A harmless dash against a stranger on a busy street will be enough to loose all your bank balance!





 Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
Gartner and G2 recommends Appknox | See how we can help you with a free Demo!
 Rohan Mendiratta
Rohan Mendiratta










_HighPerformer_HighPerformer.png)
_BestEstimatedROI_Roi.png)

